Emerging state-affiliated threats in the age of AI

This week, OpenAI and Microsoft stopped five "state-affiliated" actors with fancy names such as 'Salmon Typhoon' and 'Emerald Sleet', from abusing AI services offered by OpenAI.
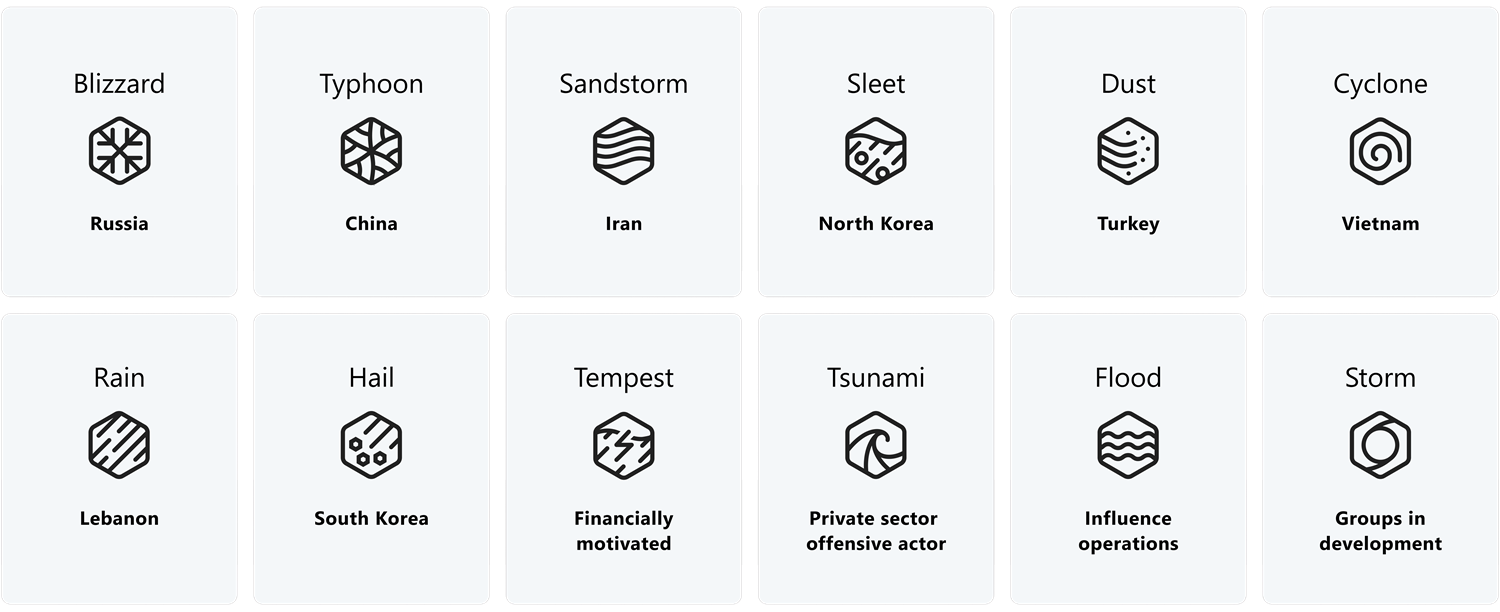
'Microsoft Threat Intelligence', a global network of security experts, "tracks more than 300 unique threat actors, including 160 nation-state actors, 50 ransomware groups, and many others", and based on information from this network, OpenAI disrupted services linked to:
- Two China-affiliated threat actors known as Charcoal Typhoon and Salmon Typhoon;
- The Iran-affiliated threat actor known as Crimson Sandstorm;
- The North Korea-affiliated actor known as Emerald Sleet;
- The Russia-affiliated actor known as Forest Blizzard.
Microsoft says that its technology "has not identified significant attacks employing the LLMs (Large Language Models) [they] monitor closely". Despite this, they believe that it is important to "expose early-stage, incremental moves that [they] observe well-known threat actors attempting, and share information on how [they] are blocking and countering them with the defender community".
If you're wondering on where the fancy names came from, Microsoft assigns a family name to a country/region of origin tied to attribution - Typhoon indicates origin or attribution to China, for nation-state actors. For other actors, the name represents a motivation. For example, Tempest indicates financially motivated actors, as highlighted in the table below.